Syntax Used in This Course
The FOR572 course documentation uses consistent syntax styles with which you should become familiar. This section helps you to make sense of what the material conveys, so you can focus more on course material than styling.
Syntax Descriptions and Examples
Note
The commands listed in this section of the lab are just for reference, so you can become familiar with text styles used in the course materials. No need to actually run them in your SIFT Workstation VMware Image!
-
Text blocks that appear in the format shown below contain commands that you would run in the SIFT or another class VM. These code blocks include an icon to the far right that allows you to copy the contents of the block, suitable for pasting into the shell in your class VMs.
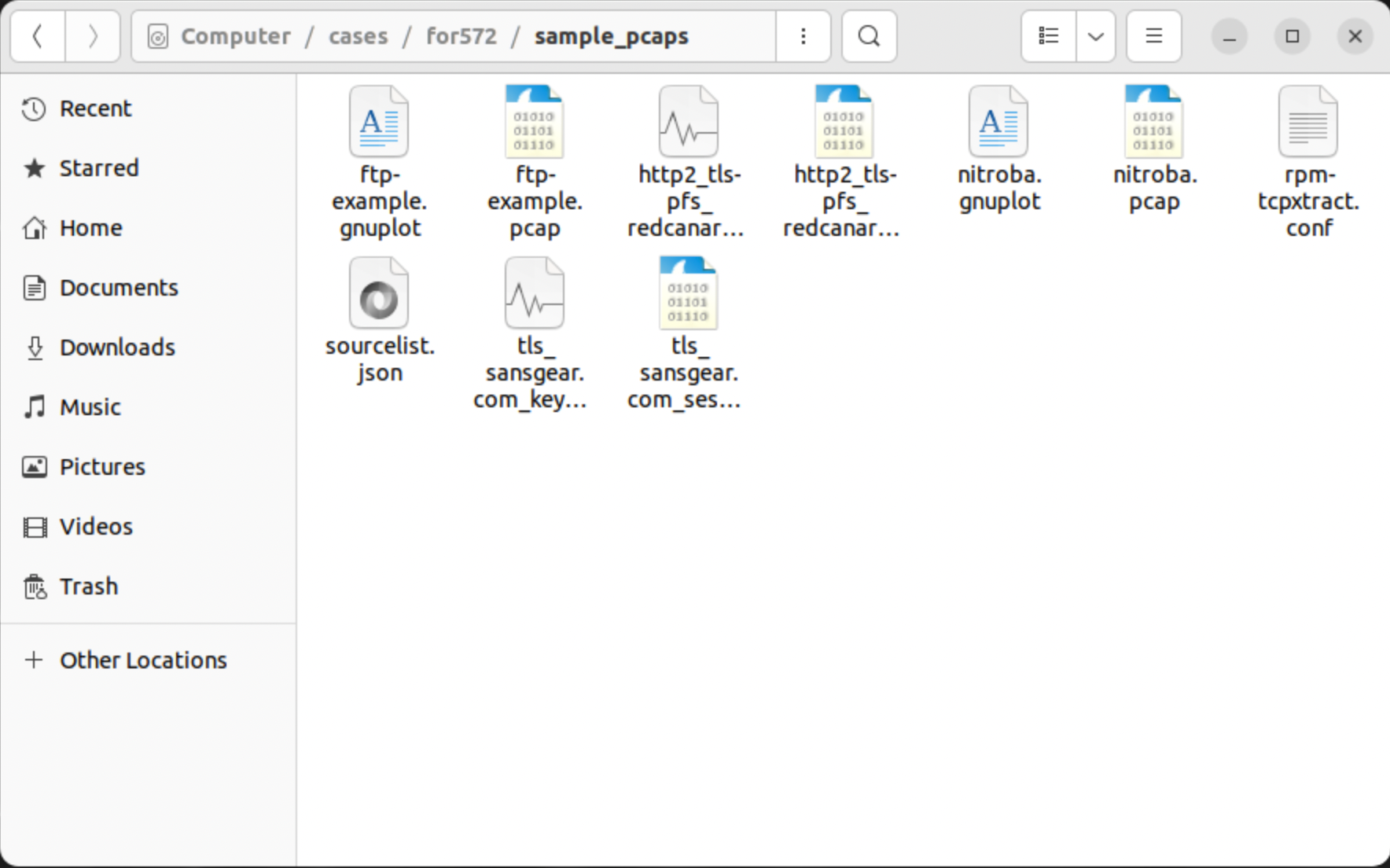
List the contents of the
/tmp/directory.Command lines
cd /tmp/ ls -lThe results are shown in a slightly different format. Results will be denoted as "Expected" or "Notional". Expected results should reflect exactly what you get from the commands shown. Notional results are shown when some variation may be present, based on lab or classroom conditions.
Notional results
sansforensics@siftworkstation: ~ $ cd /tmp/ sansforensics@siftworkstation: /tmp $ ls -l total 2836 -rw------- 1 sansforensics sansforensics 0 Apr 3 17:39 config-err-S09tBf -rw------- 1 sansforensics sansforensics 0 Jul 21 18:39 config-err-zVMGjJ -rw-r--r-- 1 root root 0 May 10 07:45 fileK8YYJh -rw-r--r-- 1 root root 0 Jun 11 07:45 fileVAP3BY -rw-r--r-- 1 root root 0 Jul 11 07:45 fileVeFMlj drwxrwxr-x 3 sansforensics sansforensics 4096 Jul 6 18:03 npm-57783-5d61223f drwxrwxr-x 3 sansforensics sansforensics 4096 Jul 6 18:04 npm-57819-3bc1b3dc ... -
Direct questions are reflected in the material as shown below.
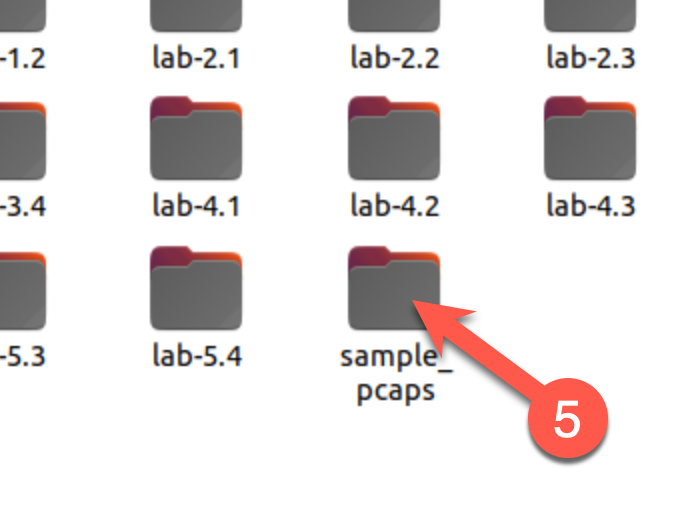
How large is the
nitroba.pcapfile, in bytes?56,795,590
Command lines
cd /cases/for572/sample_pcaps/ ls -l nitroba.pcap | awk '{print $5,$9}'Expected results
sansforensics@siftworkstation: ~ $ cd /cases/for572/sample_pcaps/ sansforensics@siftworkstation: /cases/for572/sample_pcaps $ ls -l nitroba.pcap | awk '{print $5,$9}' 56795590 nitroba.pcapWhat is the file's MD5 hash value?
d6b5df10fc572b54ceb9c543d11f10a4Command lines
md5sum nitroba.pcapExpected results
sansforensics@siftworkstation: /cases/for572/sample_pcaps $ md5sum nitroba.pcap d6b5df10fc572b54ceb9c543d11f10a4 nitroba.pcapNarrative answers are shown in bold as shown below.
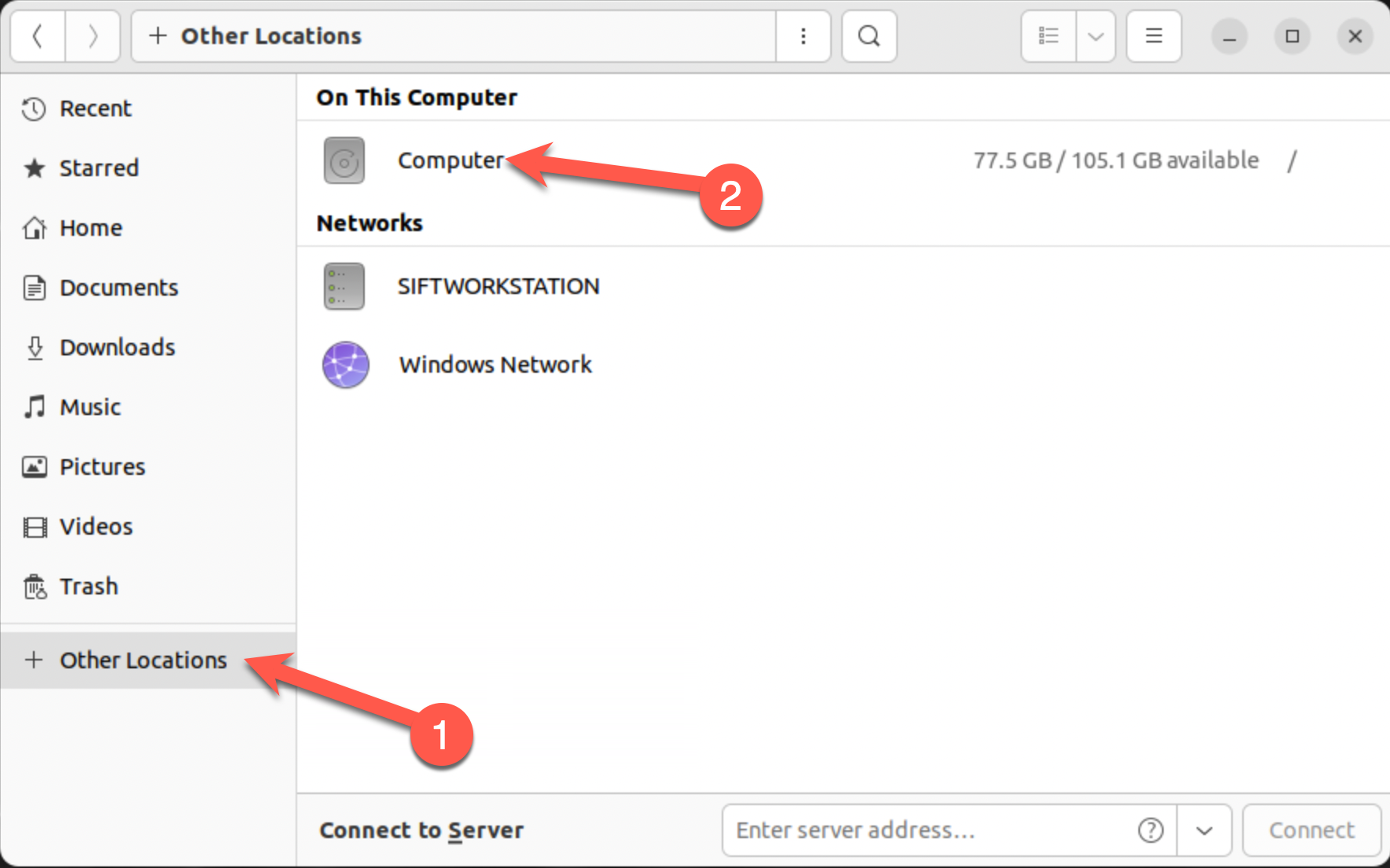
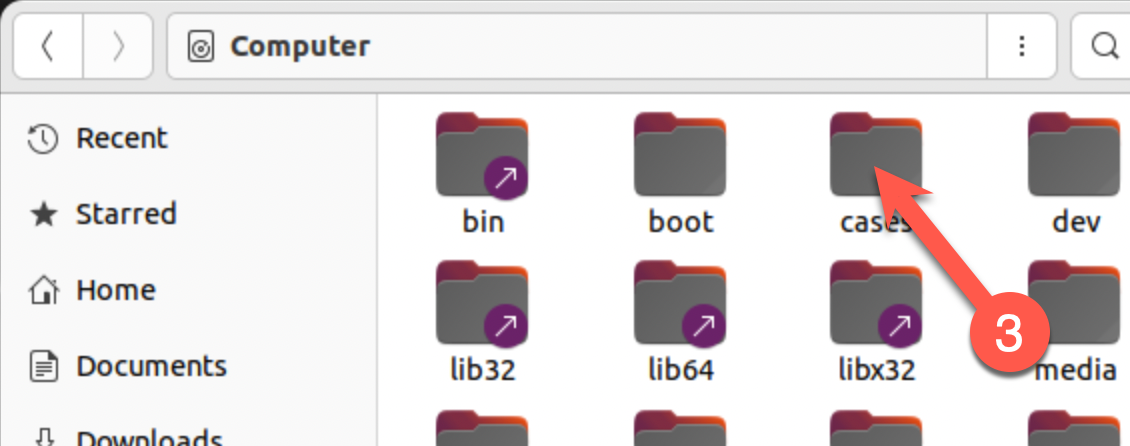
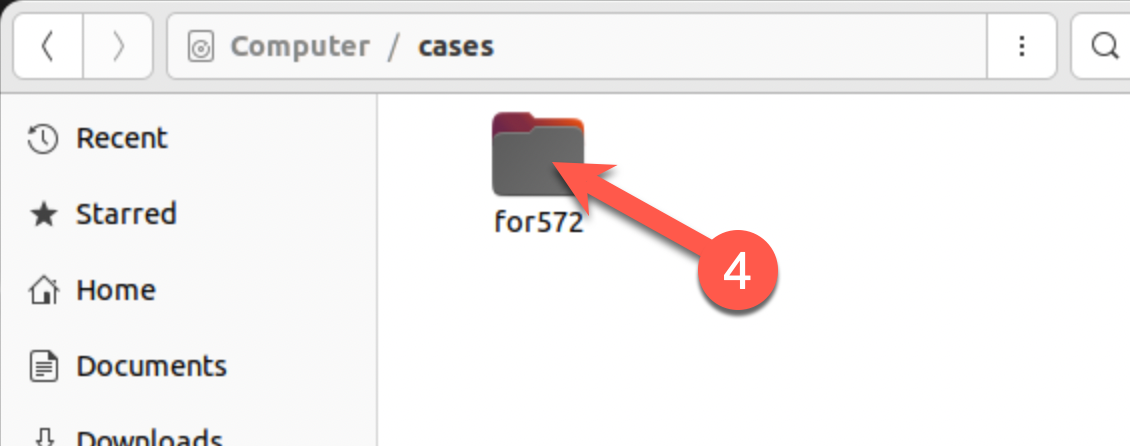
What are two ways to see the contents of the
/cases/for572/sample_pcaps/directory?The bash shell's
cdandlscommands provide one way, and the Ubuntu GUI file manager interface is another.Command lines
ls -l /cases/for572/sample_pcaps/Expected results
sansforensics@siftworkstation: /cases/for572/sample_pcaps $ ls -l /cases/for572/sample_pcaps/ total 103040 -rw-r--r-- 1 sansforensics sansforensics 449 Aug 21 19:38 ftp-example.gnuplot -rw-r--r-- 1 sansforensics sansforensics 36114110 Nov 22 2013 ftp-example.pcap -rw-r--r-- 1 sansforensics sansforensics 9081 Mar 1 2019 http2_tls-pfs_redcanary.com_keys.log -rw-r--r-- 1 sansforensics sansforensics 6071641 Mar 1 2019 http2_tls-pfs_redcanary.com_session.pcap -rw-r--r-- 1 sansforensics sansforensics 488 Aug 21 19:43 nitroba.gnuplot -rw-r--r-- 1 sansforensics sansforensics 56795590 Jul 13 20:02 nitroba.pcap -rw-r--r-- 1 sansforensics sansforensics 116 Aug 1 2016 rpm-tcpxtract.conf -rw-r--r-- 1 sansforensics sansforensics 1096 Aug 25 00:53 sourcelist.json -rw-r--r-- 1 sansforensics sansforensics 62775 Jul 8 02:18 tls_sansgear.com_keys.log -rw-r--r-- 1 sansforensics sansforensics 6427580 Jul 8 02:18 tls_sansgear.com_session.pcapGUI file manager
-
When referring to literal strings inline with narrative text, the strings will be in depicted in Courier New font. For example, a search string of
(destination_bytes >= 6000000 and destination_bytes <= 7000000)might be noted in the material inline as shown in this sentence, or via a call-out box as shown below:Kibana search string
(destination_bytes >= 6000000 and destination_bytes <= 7000000) -
Some commands follow a "template" format, in which you will replace a part of the template with content you've discovered previously in the lab. These template command lines will include placeholders surrounded by the
<%and%>enclosures with uppercase letters between them. This is an indication that you must alter the template command accordingly. For example, in the following command, you'd replace the<%IP_ADDRESS%>portion of the IP address with some information identified elsewhere in the lab.Command lines
tcpdump -n -r input.pcap -w singlehost.pcap 'host <%IP_ADDRESS%>' -
It is generally unadvisable to use the
rootadministrative account for normal activities. We will follow best practices and use thesudoutility to perform administrative actions within the SIFT VM environment wherever needed. Thesansforensicsuser has fullsudoaccess to provide a reasonable balance between best practices and a practical classroom-based lab environment. -
In the electronic workbook, some images are clickable, resulting in an enlarged version. This can be helpful when examining a detailed diagram or screenshot. These images are denoted with a magnifying glass icon in the lower-right corner. An example of this is below. In this example, the large dimensions of the screenshot even allow multiple "zoom in" stages to see all the included details.